Monero Mining Malware Finds Success at Top of Google Search
A years-long monero malware campaign has been detected for the first time inside fake Google apps placed prominently in search results

Source: Shutterstock
- Nitrokod is currently featured at the top of Google search results for popular apps, including Translate
- The malware maliciously mines monero using users’ computer resources, echoing once-prolific CoinHive
An insidious malware campaign targeting users searching for Google applications has infected thousands of computers globally to mine privacy-focused crypto monero (XMR).
You’ve probably never heard of Nitrokod. Israeli-based cyber intelligence firm Check Point Research (CPR) stumbled upon the malware last month.
In a report on Sunday, the firm said Nitrokod initially masks itself as a free software, having found remarkable success at the top of Google search results for “Google Translate desktop download.”
Also known as cryptojacking, mining malware has been used to infiltrate unsuspecting user’s machines since at least 2017, when they rose to prominence alongside crypto’s popularity.
CPR previously detected well-known cryptojacking malware CoinHive, which also mined XMR, in November of that year. CoinHive was said to be stealing 65% of an end-user’s total CPU resources without their knowledge. Academics calculated the malware was generating $250,000 per month at its peak, with the bulk of it going to less than a dozen individuals.
As for Nitrokod, CPR believes it was deployed by a Turkish-speaking entity sometime in 2019. It operates across seven stages as it moves along its path to avoid detection from typical antivirus programs and system defenses.
“The malware is easily dropped from software found on top Google search results for legitimate applications,” the firm wrote in its report.
Softpedia and Uptodown were found to be two major sources of fake applications. Blockworks has reached out to Google to learn more about how it filters these kinds of threats.
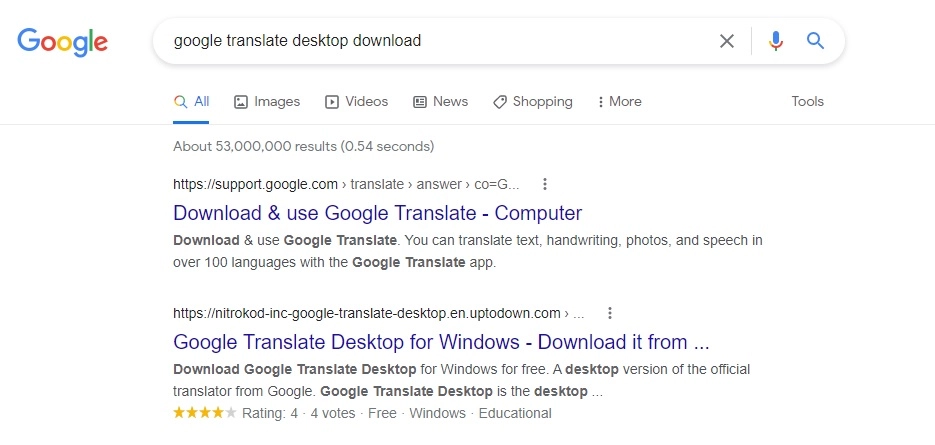 Image source: Check Point Research
Image source: Check Point Research
After downloading the application, an installer executes a delayed dropper and continuously updates itself on every restart. On the fifth day, the delayed dropper extracts an encrypted file.
The file then initiates Nitrokod’s final stages, which sets about scheduling tasks, clearing logs and adding exceptions to antivirus firewalls once 15 days have ticked by.
Finally, crypto mining malware “powermanager.exe” is surrepticiously dropped onto the infected machine and sets about generating crypto using open source Monero-based CPU miner XMRig (the same one used by CoinHive).
“After the initial software installation, the attackers delayed the infection process for weeks and deleted traces from the original installation,” the firm wrote in its report. “This allowed the campaign to successfully operate under the radar for years.”
Details of how to clean machines infected with Nitrokod can be found at the end of CPR’s threat report.
Learn More: Can Crypto Mixers and Privacy Coins Resist Censorship?
Get the news in your inbox. Explore Blockworks newsletters:
- The Breakdown: Decoding crypto and the markets. Daily.
- 0xResearch: Alpha in your inbox. Think like an analyst.