Secret Network Crypto Transactions Not So Secret After All
Secret Network was supposed to keep transactions private, but researchers warn there’s no telling how many people have decrypted them
Source: Shutterstock
Privacy-focused protocol Secret Network — intended to be anonymous and confidential — has disclosed a security vulnerability that threatened to reveal user transaction histories.
The bug, discovered by researchers from the University of Illinois Urbana-Champaign in October, allowed extraction of a so-called “consensus seed,” effectively a master decryption key for Secret Network.
“Exposure of the consensus seed would enable the complete retroactive disclosure of all Secret-4 private transactions since the chain began,” the team said. SCRT Labs, the group behind the blockchain’s development, patched the vulnerability earlier this month.
The attack vector involved exploiting flaws in Intel’s Software Guard Extension (SGX). SGX is a set of security-related instruction codes built into some Intel central processing units (CPUs), including their latest 10th, 11th and 12th-generation chips.
The SGX bugs first became public knowledge in early August, and the researchers say they also discovered related flaws in video software PowerDVD.
Secret Network, backed by scandal-ridden firms Alameda Research and Terraform Labs, runs on delegated proof-of-stake consensus, a method first utilized by EOS. The protocol is considered somewhat of a competitor to other privacy-centric networks such as Monero and Zcash, albeit with a much smaller market capitalization around $150 million (compared to $2.5 billion and $550 million).
Unlike Bitcoin and Ethereum, which allow anyone with the right equipment (and in the latter’s case, enough ether) to join the network, Secret Network token holders select 50 trusted third parties to maintain specialized validating nodes that keep the blockchain flowing.
But the researchers didn’t have to become fully-fledged network validators to exploit the bug. They were able to extract their Secret Network master key by running a full node (which anyone can do) with a machine powered by the vulnerable processors.
Full nodes download a complete copy of the blockchain onto the related machine, and in Secret Network’s case, a “sealed consensus seed” along with it.
Secret Network node software uses what’s known as a trusted execution environment (TEE). These are secure regions of a main processor that only certain trusted devices, codes, or applications can access. The researchers were able to exploit this part of Secret Network’s stack, alongside Intel’s SGX, to decrypt the sealed consensus seed and thus reveal all private transactions on the protocol’s ledger.
Secret Network users urged to reconsider their operational security
SCRT Labs has assured users that to the best of its knowledge, no malicious actor had exploited the vulnerability in the wild prior to it being patched.
The researchers, however, have stated there’s no way to know for certain whether the attack had been executed previously.
SCRT said it held off releasing details of the bug due to a mutual agreement between itself, Intel and the researchers to mitigate potential for the vulnerability to be exploited, a common move in software development.
In any case, the team that discovered the flaw have urged “privacy-conscious” users to reassess their online footprints, considering that their past “secret” transactions may be exposed.
“SCRT Labs ‘fixed’ it now, but all past transactions are compromised,” the team said. Secret Network’s native token has remained relatively steady since the disclosure, only dropping around 2%, although it’s already collapsed 85% in the year to date alongside swathes of other crypto projects.
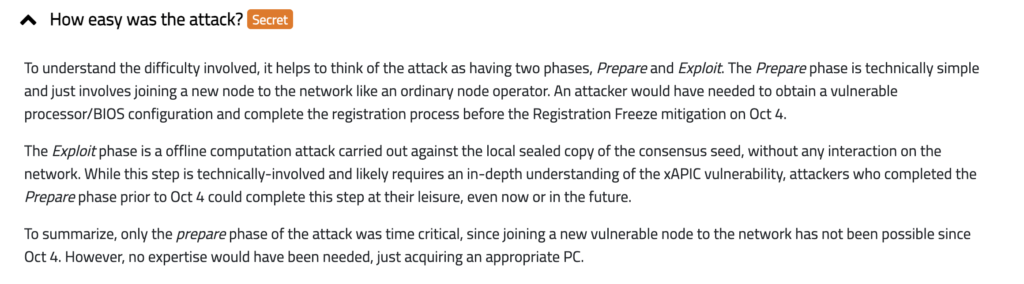 The researchers break down the attack into two phases: Prepare and Exploit | Source: SGX.fail
The researchers break down the attack into two phases: Prepare and Exploit | Source: SGX.fail
New Secret Network nodes are currently limited to “server-class” hardware while SCRT has vowed to ratchet security-focused features for the network. The stewards also said they would strengthen their communications with Intel to ensure users receive early warning of future undisclosed vulnerabilities.
Funds on Secret Network are considered safe (only the confidentiality of the network has been compromised, not user private keys). The researchers noted the most concerning application of the attack is bulk surveillance of Secret users’ personal finances.
There was still opportunity to front-run DeFi applications and breach private metadata tied to NFTs deployed on the network. “Any digital assets that rely on private metadata, such as NFTs exchanging secret authentication keys, would be at risk of theft,” they wrote.
David Canellis contributed reporting.
Get the news in your inbox. Explore Blockworks newsletters:
- The Breakdown: Decoding crypto and the markets. Daily.
- 0xResearch: Alpha in your inbox. Think like an analyst.






